Quick filters:
User authentication Stock Photos and Images
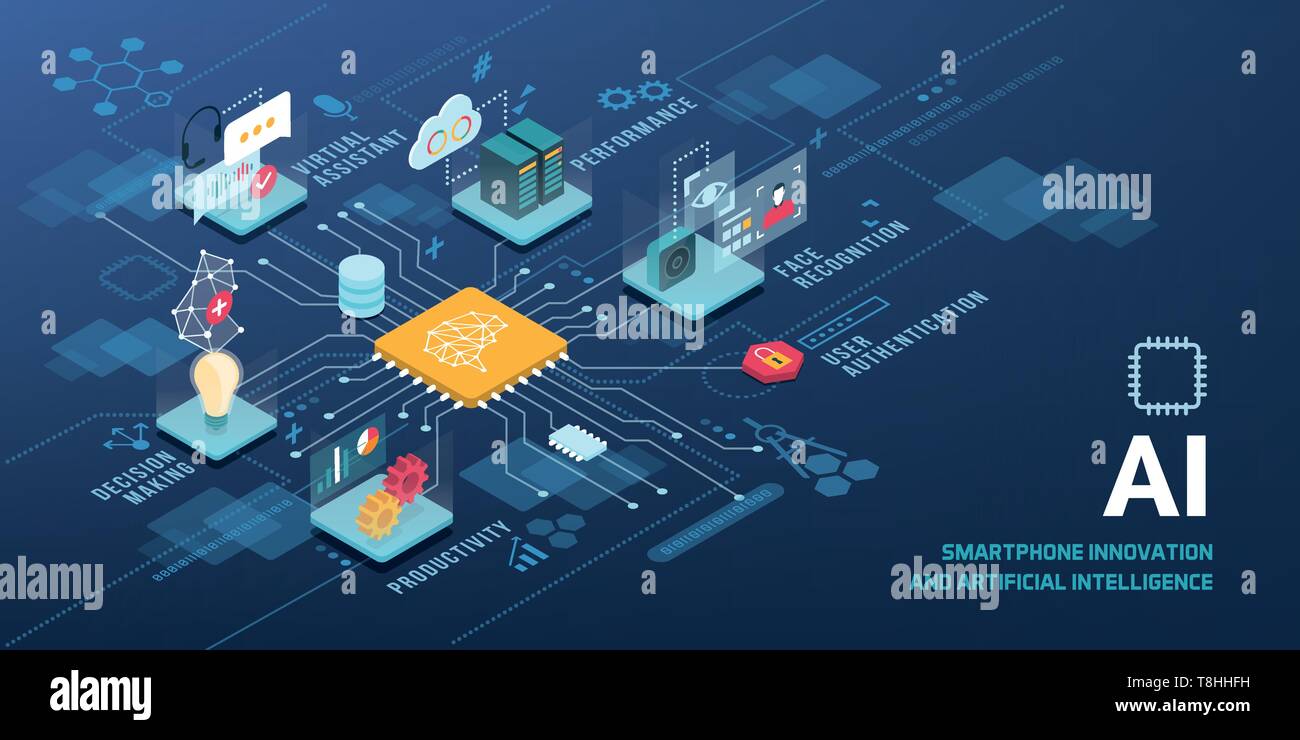 AI technology innovative applications vector infographic: virtual assistant, performance optimization, user authentication, productivity, decision mak Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/ai-technology-innovative-applications-vector-infographic-virtual-assistant-performance-optimization-user-authentication-productivity-decision-mak-image246249349.html
AI technology innovative applications vector infographic: virtual assistant, performance optimization, user authentication, productivity, decision mak Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/ai-technology-innovative-applications-vector-infographic-virtual-assistant-performance-optimization-user-authentication-productivity-decision-mak-image246249349.htmlRFT8HHFH–AI technology innovative applications vector infographic: virtual assistant, performance optimization, user authentication, productivity, decision mak
 cyber security - woman using mobile application in smartphone for internet banking user authentication Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-woman-using-mobile-application-in-smartphone-for-internet-banking-user-authentication-image366025223.html
cyber security - woman using mobile application in smartphone for internet banking user authentication Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cyber-security-woman-using-mobile-application-in-smartphone-for-internet-banking-user-authentication-image366025223.htmlRF2C7DTWB–cyber security - woman using mobile application in smartphone for internet banking user authentication
 Password and username login page, secure access on internet. Online user authentication sign-in, cyber security, data protection. Finger touching lock Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/password-and-username-login-page-secure-access-on-internet-online-user-authentication-sign-in-cyber-security-data-protection-finger-touching-lock-image502960056.html
Password and username login page, secure access on internet. Online user authentication sign-in, cyber security, data protection. Finger touching lock Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/password-and-username-login-page-secure-access-on-internet-online-user-authentication-sign-in-cyber-security-data-protection-finger-touching-lock-image502960056.htmlRF2M67PK4–Password and username login page, secure access on internet. Online user authentication sign-in, cyber security, data protection. Finger touching lock
 Executive Pressing USER AUTHENTICATION Onscreen Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-executive-pressing-user-authentication-onscreen-103619808.html
Executive Pressing USER AUTHENTICATION Onscreen Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-executive-pressing-user-authentication-onscreen-103619808.htmlRFG0G83C–Executive Pressing USER AUTHENTICATION Onscreen
 Flat login interface is showing over dusk skyline with username or password fields and green button Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/flat-login-interface-is-showing-over-dusk-skyline-with-username-or-password-fields-and-green-button-image682954749.html
Flat login interface is showing over dusk skyline with username or password fields and green button Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/flat-login-interface-is-showing-over-dusk-skyline-with-username-or-password-fields-and-green-button-image682954749.htmlRF3BK37N1–Flat login interface is showing over dusk skyline with username or password fields and green button
RF3CHNB4Y–Password Security Icon – Padlock Symbol for Data Protection and User Authentication. Vector Illustration
 User Authentication text engraved on wooden blocks with padlock and PC keyboard background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-text-engraved-on-wooden-blocks-with-padlock-and-pc-keyboard-background-image621135373.html
User Authentication text engraved on wooden blocks with padlock and PC keyboard background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-text-engraved-on-wooden-blocks-with-padlock-and-pc-keyboard-background-image621135373.htmlRF2Y2F4E5–User Authentication text engraved on wooden blocks with padlock and PC keyboard background.
 User authentication system with username and password cyber security concept Security technology protects personal information. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-system-with-username-and-password-cyber-security-concept-security-technology-protects-personal-information-image592297140.html
User authentication system with username and password cyber security concept Security technology protects personal information. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-system-with-username-and-password-cyber-security-concept-security-technology-protects-personal-information-image592297140.htmlRF2WBHD18–User authentication system with username and password cyber security concept Security technology protects personal information.
 Woman with smartphone protection with two factor authentication. Cybersecurity and privacy protect data. Personal online privacy. Cyber hacker threat. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-with-smartphone-protection-with-two-factor-authentication-cybersecurity-and-privacy-protect-data-personal-online-privacy-cyber-hacker-threat-image566042902.html
Woman with smartphone protection with two factor authentication. Cybersecurity and privacy protect data. Personal online privacy. Cyber hacker threat. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-with-smartphone-protection-with-two-factor-authentication-cybersecurity-and-privacy-protect-data-personal-online-privacy-cyber-hacker-threat-image566042902.htmlRF2RTWDDX–Woman with smartphone protection with two factor authentication. Cybersecurity and privacy protect data. Personal online privacy. Cyber hacker threat.
RF3BN6E16–Smartwatch with Fingerprint Scanner Icon for Biometric Security, User Authentication, and Secure Mobile Payments
 ID Verification Illustration – Man in Suit with ID Card and Magnifying Glass Highlighting Green Checkmark Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/id-verification-illustration-man-in-suit-with-id-card-and-magnifying-glass-highlighting-green-checkmark-image682294972.html
ID Verification Illustration – Man in Suit with ID Card and Magnifying Glass Highlighting Green Checkmark Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/id-verification-illustration-man-in-suit-with-id-card-and-magnifying-glass-highlighting-green-checkmark-image682294972.htmlRF3BJ165G–ID Verification Illustration – Man in Suit with ID Card and Magnifying Glass Highlighting Green Checkmark
RF2M1F47G–Employee clerk card, id card icon, vcard vector icon illustration for graphic design, logo, web site, social media, mobile app, ui
 Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image259397975.html
Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image259397975.htmlRFW20GNB–Remote Authentication in Dial In User Service. Telecommunications Networks Concept.
 User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image548936506.html
User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image548936506.htmlRF2PW2636–User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security
 Cybersecurity technology for protecting data, secure login, user authentication, and privacy control. Emphasizes digital safety, identity protection, Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cybersecurity-technology-for-protecting-data-secure-login-user-authentication-and-privacy-control-emphasizes-digital-safety-identity-protection-image684767119.html
Cybersecurity technology for protecting data, secure login, user authentication, and privacy control. Emphasizes digital safety, identity protection, Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cybersecurity-technology-for-protecting-data-secure-login-user-authentication-and-privacy-control-emphasizes-digital-safety-identity-protection-image684767119.htmlRF3BP1RCF–Cybersecurity technology for protecting data, secure login, user authentication, and privacy control. Emphasizes digital safety, identity protection,
 Mobile security and privacy isometric landing page vector template. Personal data encryption and cybersecurity 3d concept. Online security and internet safety. Smartphone password, user authentication Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/mobile-security-and-privacy-isometric-landing-page-vector-template-personal-data-encryption-and-cybersecurity-3d-concept-online-security-and-internet-safety-smartphone-password-user-authentication-image366011071.html
Mobile security and privacy isometric landing page vector template. Personal data encryption and cybersecurity 3d concept. Online security and internet safety. Smartphone password, user authentication Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/mobile-security-and-privacy-isometric-landing-page-vector-template-personal-data-encryption-and-cybersecurity-3d-concept-online-security-and-internet-safety-smartphone-password-user-authentication-image366011071.htmlRF2C7D6RY–Mobile security and privacy isometric landing page vector template. Personal data encryption and cybersecurity 3d concept. Online security and internet safety. Smartphone password, user authentication
 the phone requires user authentication. as a face or fingerprint scan Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-phone-requires-user-authentication-as-a-face-or-fingerprint-scan-image370549423.html
the phone requires user authentication. as a face or fingerprint scan Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/the-phone-requires-user-authentication-as-a-face-or-fingerprint-scan-image370549423.htmlRF2CERYFY–the phone requires user authentication. as a face or fingerprint scan
 User Authentication text engraved on wooden blocks with padlock and PC keyboard background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-text-engraved-on-wooden-blocks-with-padlock-and-pc-keyboard-background-image687592572.html
User Authentication text engraved on wooden blocks with padlock and PC keyboard background Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-text-engraved-on-wooden-blocks-with-padlock-and-pc-keyboard-background-image687592572.htmlRF3BXJF9G–User Authentication text engraved on wooden blocks with padlock and PC keyboard background
 Log user interface, Login page, users typing passwords navigate, login access, username and password field, application sign in, login interface Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/log-user-interface-login-page-users-typing-passwords-navigate-login-access-username-and-password-field-application-sign-in-login-interface-image633376904.html
Log user interface, Login page, users typing passwords navigate, login access, username and password field, application sign in, login interface Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/log-user-interface-login-page-users-typing-passwords-navigate-login-access-username-and-password-field-application-sign-in-login-interface-image633376904.htmlRF2YPCPKM–Log user interface, Login page, users typing passwords navigate, login access, username and password field, application sign in, login interface
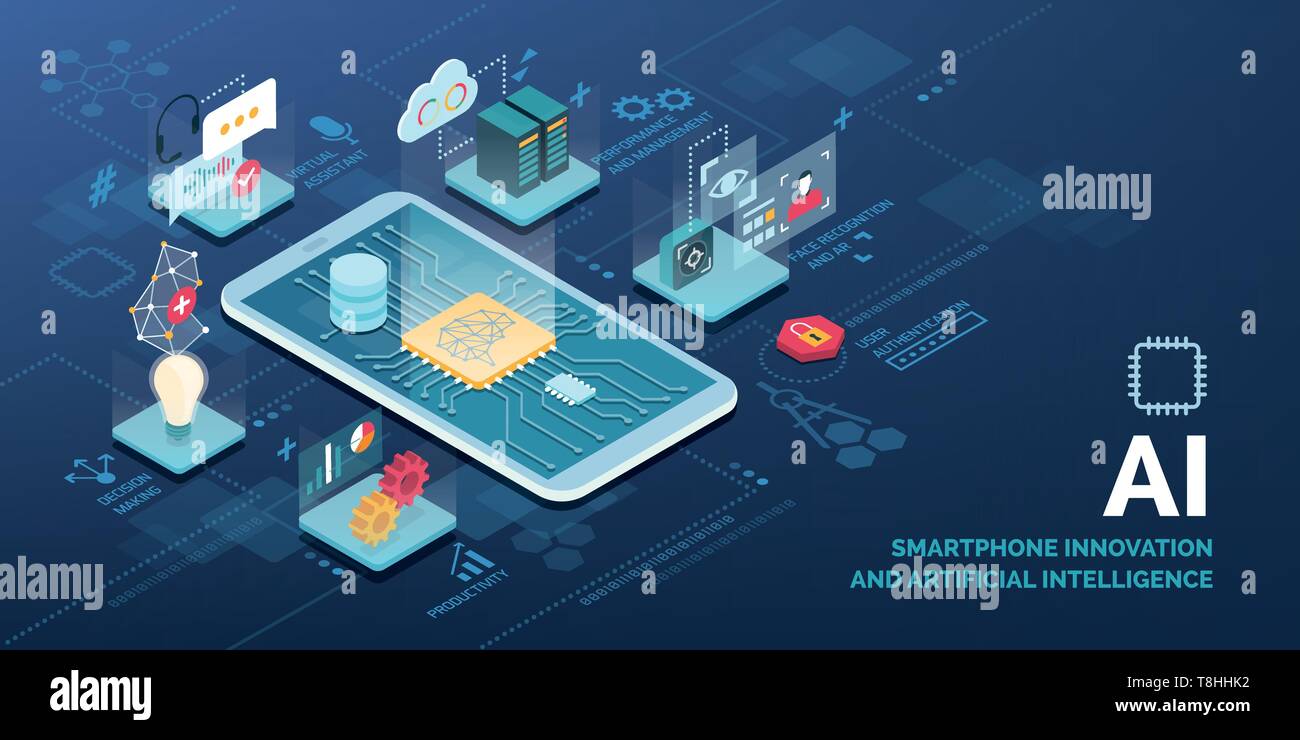 Innovative smartphone with AI applications vector infographic: virtual assistant, performance optimization, user authentication, productivity, decisio Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/innovative-smartphone-with-ai-applications-vector-infographic-virtual-assistant-performance-optimization-user-authentication-productivity-decisio-image246249446.html
Innovative smartphone with AI applications vector infographic: virtual assistant, performance optimization, user authentication, productivity, decisio Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/innovative-smartphone-with-ai-applications-vector-infographic-virtual-assistant-performance-optimization-user-authentication-productivity-decisio-image246249446.htmlRFT8HHK2–Innovative smartphone with AI applications vector infographic: virtual assistant, performance optimization, user authentication, productivity, decisio
 User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image501282267.html
User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image501282267.htmlRF2M3FAJ3–User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security
RF2YAHADH–User Profile Icon with Verified Checkmark Symbol.
RF2NM087W–Man and woman avatar profile. Male and Female face silhouette. Profile picture, portrait symbol. User member. Circle button with avatar.
 Security scan and cybersecurity authentication as a biometrics recognition and access technology concept in a 3D illustration style. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-scan-and-cybersecurity-authentication-as-a-biometrics-recognition-and-access-technology-concept-in-a-3d-illustration-style-image187020424.html
Security scan and cybersecurity authentication as a biometrics recognition and access technology concept in a 3D illustration style. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/security-scan-and-cybersecurity-authentication-as-a-biometrics-recognition-and-access-technology-concept-in-a-3d-illustration-style-image187020424.htmlRFMT7ECT–Security scan and cybersecurity authentication as a biometrics recognition and access technology concept in a 3D illustration style.
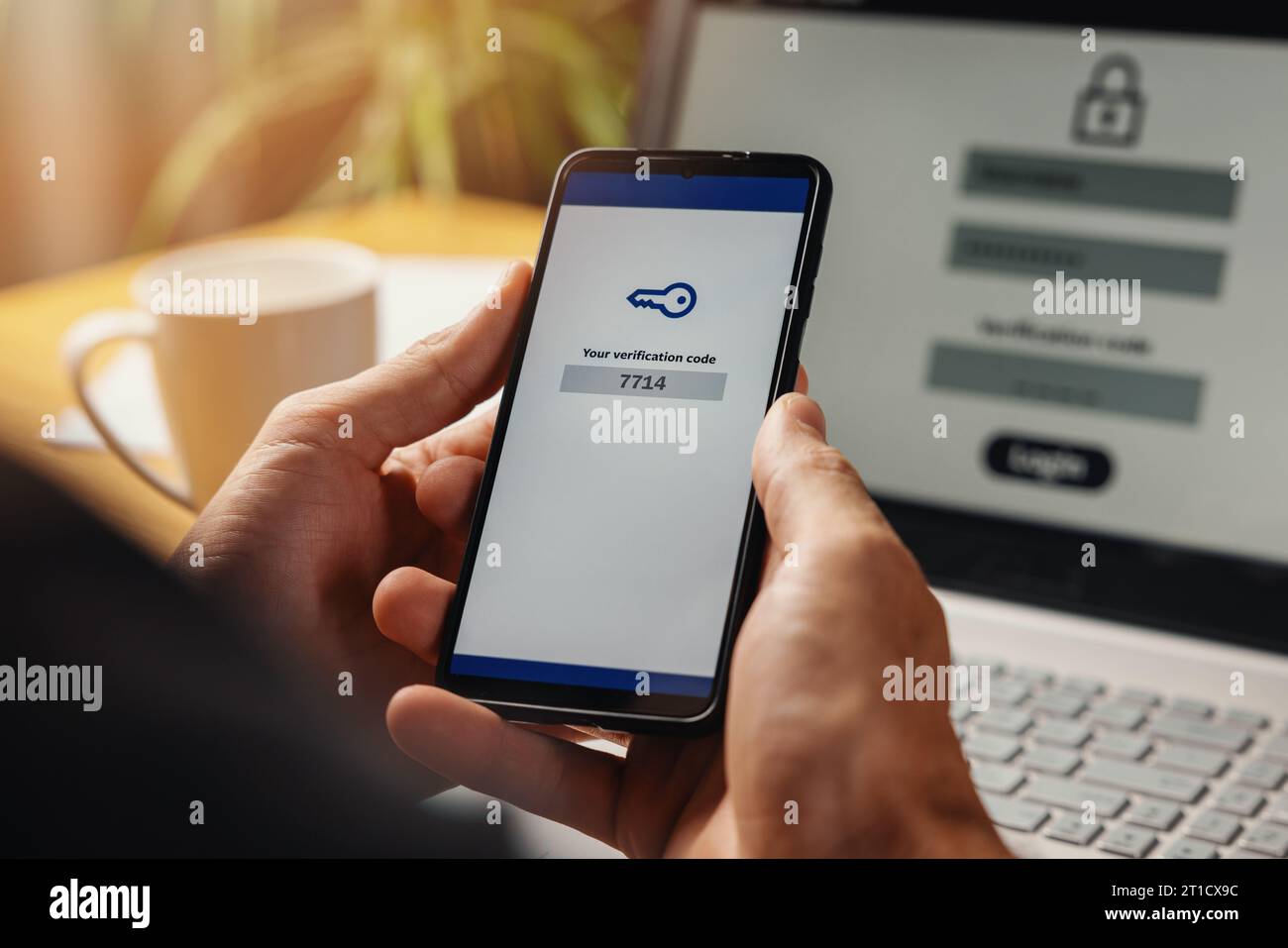 two-step authentication. verification code on smart phone screen for identity identification for online banking. cyber security technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-authentication-verification-code-on-smart-phone-screen-for-identity-identification-for-online-banking-cyber-security-technology-image568840872.html
two-step authentication. verification code on smart phone screen for identity identification for online banking. cyber security technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-authentication-verification-code-on-smart-phone-screen-for-identity-identification-for-online-banking-cyber-security-technology-image568840872.htmlRF2T1CX9C–two-step authentication. verification code on smart phone screen for identity identification for online banking. cyber security technology
 Man entering code on a board with blue buttons. Composite image between a hand photography and a 3D background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/man-entering-code-on-a-board-with-blue-buttons-composite-image-between-a-hand-photography-and-a-3d-background-image442642289.html
Man entering code on a board with blue buttons. Composite image between a hand photography and a 3D background. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/man-entering-code-on-a-board-with-blue-buttons-composite-image-between-a-hand-photography-and-a-3d-background-image442642289.htmlRF2GM42N5–Man entering code on a board with blue buttons. Composite image between a hand photography and a 3D background.
 User authentication system with username and password cyber security concept Security technology protects personal information. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-system-with-username-and-password-cyber-security-concept-security-technology-protects-personal-information-image592297075.html
User authentication system with username and password cyber security concept Security technology protects personal information. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-system-with-username-and-password-cyber-security-concept-security-technology-protects-personal-information-image592297075.htmlRF2WBHCXY–User authentication system with username and password cyber security concept Security technology protects personal information.
 Woman use digital tablet to login with holographic authentication interface. Cyber security concept. Data protection and secured internet access. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-use-digital-tablet-to-login-with-holographic-authentication-interface-cyber-security-concept-data-protection-and-secured-internet-access-image574477320.html
Woman use digital tablet to login with holographic authentication interface. Cyber security concept. Data protection and secured internet access. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-use-digital-tablet-to-login-with-holographic-authentication-interface-cyber-security-concept-data-protection-and-secured-internet-access-image574477320.htmlRF2TAHKK4–Woman use digital tablet to login with holographic authentication interface. Cyber security concept. Data protection and secured internet access.
RF3BMTP8F–Mobile Pattern Lock Screen Icon with Connecting Dots Grid for Smartphone Security, User Authentication, and Device Access
 Hand turns dice and changes the abbreviation 1FA (One factor authentication) to 2FA (Two factor authentication). Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-turns-dice-and-changes-the-abbreviation-1fa-one-factor-authentication-to-2fa-two-factor-authentication-image574394357.html
Hand turns dice and changes the abbreviation 1FA (One factor authentication) to 2FA (Two factor authentication). Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/hand-turns-dice-and-changes-the-abbreviation-1fa-one-factor-authentication-to-2fa-two-factor-authentication-image574394357.htmlRF2TADWT5–Hand turns dice and changes the abbreviation 1FA (One factor authentication) to 2FA (Two factor authentication).
RF2PGW020–User protection icon. Privacy symbol concept isolated on white background. Vector illustration
 Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image248247055.html
Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image248247055.htmlRFTBTHJ7–Remote Authentication in Dial In User Service. Telecommunications Networks Concept.
 User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image549053465.html
User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image549053465.htmlRF2PW7F89–User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security
 Laptop with authorization on the screen. Login and password of the user. Login to the system or account. Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-laptop-with-authorization-on-the-screen-login-and-password-of-the-172885132.html
Laptop with authorization on the screen. Login and password of the user. Login to the system or account. Vector illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-laptop-with-authorization-on-the-screen-login-and-password-of-the-172885132.htmlRFM17GN0–Laptop with authorization on the screen. Login and password of the user. Login to the system or account. Vector illustration
RF2S97FRK–Digital security lock and fingerprint image over network connections and user icons
 Authentication code for log into website user account flat vector illustration, OTP, Authentication password, One-time password for secure transaction Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-code-for-log-into-website-user-account-flat-vector-illustration-otp-authentication-password-one-time-password-for-secure-transaction-image633929142.html
Authentication code for log into website user account flat vector illustration, OTP, Authentication password, One-time password for secure transaction Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-code-for-log-into-website-user-account-flat-vector-illustration-otp-authentication-password-one-time-password-for-secure-transaction-image633929142.htmlRF2YR9Y2E–Authentication code for log into website user account flat vector illustration, OTP, Authentication password, One-time password for secure transaction
 Smart phone with Microsoft Authenticator app to allow users login with two factor authentication. Canada, Alberta. January 18, 2021 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smart-phone-with-microsoft-authenticator-app-to-allow-users-login-with-two-factor-authentication-canada-alberta-january-18-2021-image398012967.html
Smart phone with Microsoft Authenticator app to allow users login with two factor authentication. Canada, Alberta. January 18, 2021 Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/smart-phone-with-microsoft-authenticator-app-to-allow-users-login-with-two-factor-authentication-canada-alberta-january-18-2021-image398012967.htmlRF2E3F1GR–Smart phone with Microsoft Authenticator app to allow users login with two factor authentication. Canada, Alberta. January 18, 2021
 Log user interface, Mobile Login page, users typing passwords navigate, login access, username and password field, application sign in, login mobile i Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/log-user-interface-mobile-login-page-users-typing-passwords-navigate-login-access-username-and-password-field-application-sign-in-login-mobile-i-image633377272.html
Log user interface, Mobile Login page, users typing passwords navigate, login access, username and password field, application sign in, login mobile i Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/log-user-interface-mobile-login-page-users-typing-passwords-navigate-login-access-username-and-password-field-application-sign-in-login-mobile-i-image633377272.htmlRF2YPCR4T–Log user interface, Mobile Login page, users typing passwords navigate, login access, username and password field, application sign in, login mobile i
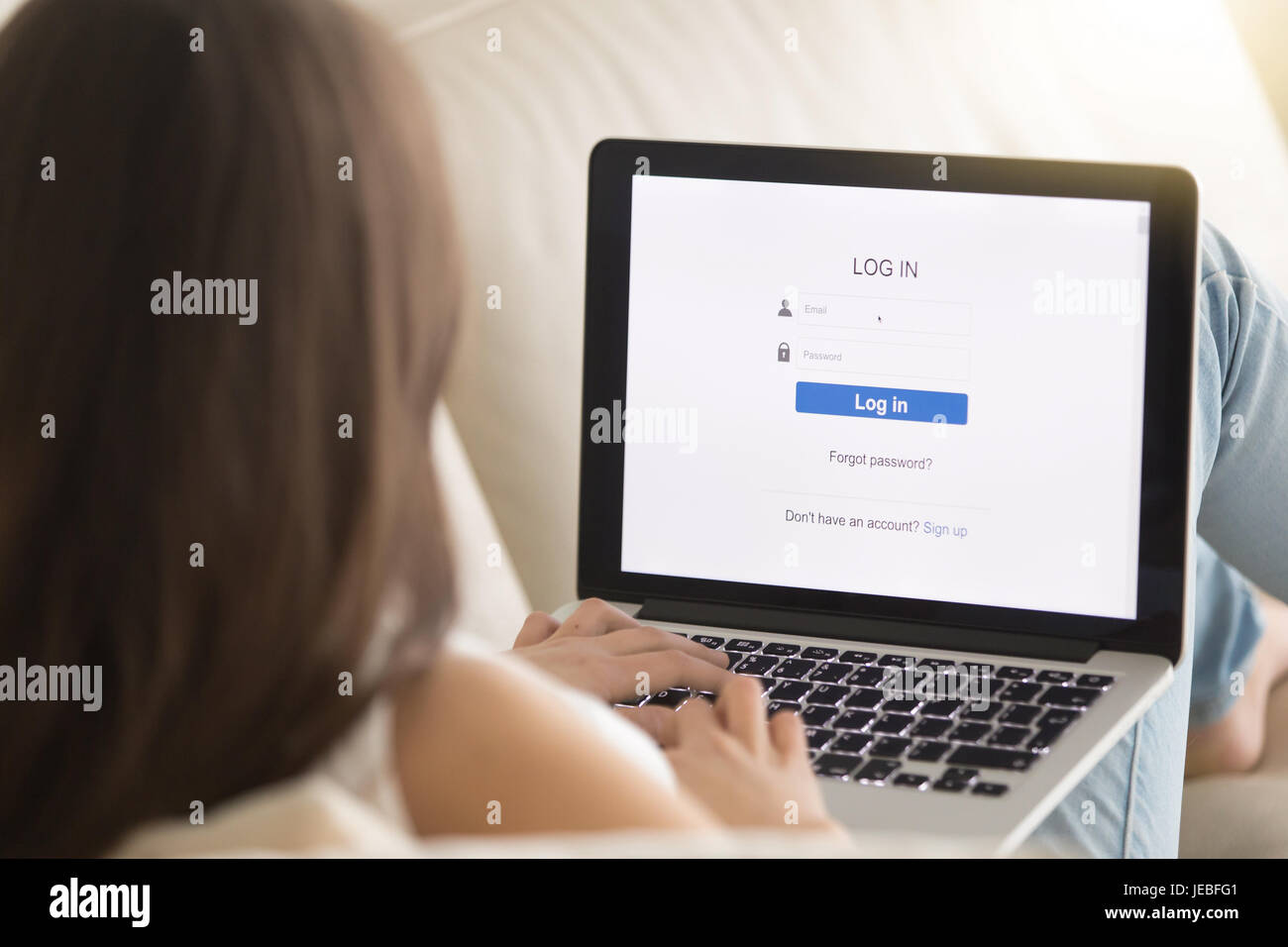 Female user passes security authorization system Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-female-user-passes-security-authorization-system-146541809.html
Female user passes security authorization system Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-female-user-passes-security-authorization-system-146541809.htmlRFJEBFG1–Female user passes security authorization system
 Person accessing a secured system using a virtual login screen, highlighting digital security, user authentication, and data protection in modern tech Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/person-accessing-a-secured-system-using-a-virtual-login-screen-highlighting-digital-security-user-authentication-and-data-protection-in-modern-tech-image678166672.html
Person accessing a secured system using a virtual login screen, highlighting digital security, user authentication, and data protection in modern tech Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/person-accessing-a-secured-system-using-a-virtual-login-screen-highlighting-digital-security-user-authentication-and-data-protection-in-modern-tech-image678166672.htmlRF3BB94E8–Person accessing a secured system using a virtual login screen, highlighting digital security, user authentication, and data protection in modern tech
 Authentication and authorization. Duo internet identity, safety multi password. Authentic isometric 3d vector concept. Illustration of verification security password Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-and-authorization-duo-internet-identity-safety-multi-password-authentic-isometric-3d-vector-concept-illustration-of-verification-security-password-image357388150.html
Authentication and authorization. Duo internet identity, safety multi password. Authentic isometric 3d vector concept. Illustration of verification security password Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-and-authorization-duo-internet-identity-safety-multi-password-authentic-isometric-3d-vector-concept-illustration-of-verification-security-password-image357388150.htmlRF2BNCC6E–Authentication and authorization. Duo internet identity, safety multi password. Authentic isometric 3d vector concept. Illustration of verification security password
RF2RC9XFA–Default Avatar Profile Picture. User profile icon. Business people. User member, People icon in flat style. Circle button with avatar photo silhouette
 Phishing and information security concept with illustrative images. Businessman holding a tablet or phone with a screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-and-information-security-concept-with-illustrative-images-businessman-holding-a-tablet-or-phone-with-a-screen-image460898760.html
Phishing and information security concept with illustrative images. Businessman holding a tablet or phone with a screen. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/phishing-and-information-security-concept-with-illustrative-images-businessman-holding-a-tablet-or-phone-with-a-screen-image460898760.htmlRF2HNRN20–Phishing and information security concept with illustrative images. Businessman holding a tablet or phone with a screen.
 Digital Identity and Security Authentication as a Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-identity-and-security-authentication-as-a-concept-image386351875.html
Digital Identity and Security Authentication as a Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-identity-and-security-authentication-as-a-concept-image386351875.htmlRF2DCFRN7–Digital Identity and Security Authentication as a Concept
 Zero trust security message on speech bubbles with a magnifying glass. Security, wifi, cloud service, mutual authentication, check, network, access Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/zero-trust-security-message-on-speech-bubbles-with-a-magnifying-glass-security-wifi-cloud-service-mutual-authentication-check-network-access-image603015764.html
Zero trust security message on speech bubbles with a magnifying glass. Security, wifi, cloud service, mutual authentication, check, network, access Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/zero-trust-security-message-on-speech-bubbles-with-a-magnifying-glass-security-wifi-cloud-service-mutual-authentication-check-network-access-image603015764.htmlRF2X11MN8–Zero trust security message on speech bubbles with a magnifying glass. Security, wifi, cloud service, mutual authentication, check, network, access
 User authentication system with username and password cyber security concept Security technology protects personal information. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-system-with-username-and-password-cyber-security-concept-security-technology-protects-personal-information-image592297177.html
User authentication system with username and password cyber security concept Security technology protects personal information. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-system-with-username-and-password-cyber-security-concept-security-technology-protects-personal-information-image592297177.htmlRF2WBHD2H–User authentication system with username and password cyber security concept Security technology protects personal information.
 Authentication Form on Laptop Screen. Vector Illustration. Window with Folders. Account Login Form with Username and Password Fields. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-form-on-laptop-screen-vector-illustration-window-with-folders-account-login-form-with-username-and-password-fields-image469393385.html
Authentication Form on Laptop Screen. Vector Illustration. Window with Folders. Account Login Form with Username and Password Fields. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-form-on-laptop-screen-vector-illustration-window-with-folders-account-login-form-with-username-and-password-fields-image469393385.htmlRF2J7JM1D–Authentication Form on Laptop Screen. Vector Illustration. Window with Folders. Account Login Form with Username and Password Fields.
 Laptop with Fingerprint and Laptop with User Security Shield on Black and White Backgrounds, Representing Digital Security or Biometric Authentication Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/laptop-with-fingerprint-and-laptop-with-user-security-shield-on-black-and-white-backgrounds-representing-digital-security-or-biometric-authentication-image682612646.html
Laptop with Fingerprint and Laptop with User Security Shield on Black and White Backgrounds, Representing Digital Security or Biometric Authentication Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/laptop-with-fingerprint-and-laptop-with-user-security-shield-on-black-and-white-backgrounds-representing-digital-security-or-biometric-authentication-image682612646.htmlRF3BJFKB2–Laptop with Fingerprint and Laptop with User Security Shield on Black and White Backgrounds, Representing Digital Security or Biometric Authentication
 Modern corporate company office employee id card or identity card design layout with blue and green color. Creative business identification card Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/modern-corporate-company-office-employee-id-card-or-identity-card-design-layout-with-blue-and-green-color-creative-business-identification-card-image696850468.html
Modern corporate company office employee id card or identity card design layout with blue and green color. Creative business identification card Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/modern-corporate-company-office-employee-id-card-or-identity-card-design-layout-with-blue-and-green-color-creative-business-identification-card-image696850468.htmlRF3CDM7TM–Modern corporate company office employee id card or identity card design layout with blue and green color. Creative business identification card
 Moody desktop photo with laptop and warm light as background with lock protection VR interface. Internet security and data protection concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/moody-desktop-photo-with-laptop-and-warm-light-as-background-with-lock-protection-vr-interface-internet-security-and-data-protection-concept-image551620746.html
Moody desktop photo with laptop and warm light as background with lock protection VR interface. Internet security and data protection concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/moody-desktop-photo-with-laptop-and-warm-light-as-background-with-lock-protection-vr-interface-internet-security-and-data-protection-concept-image551620746.htmlRF2R1CDTX–Moody desktop photo with laptop and warm light as background with lock protection VR interface. Internet security and data protection concept.
 Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image247191551.html
Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image247191551.htmlRFTA4F9K–Remote Authentication in Dial In User Service. Telecommunications Networks Concept.
 User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image548797795.html
User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-authentication-cybersecurity-information-security-and-encryption-technology-personal-data-onlinecomputer-system-firewall-and-internet-security-image548797795.htmlRF2PTRW57–User authentication cybersecurity information security and encryption, technology personal data online.computer system firewall and internet security
 Login user interface Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/login-user-interface-image210196705.html
Login user interface Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/login-user-interface-image210196705.htmlRFP5Y815–Login user interface
 User interface form set Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-user-interface-form-set-81316383.html
User interface form set Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/stock-photo-user-interface-form-set-81316383.htmlRFEM87TF–User interface form set
RF2WAW8HW–Login icon, user interface account login, vector user symbol.
RF3BNHRMW–'ID Card Icons - Profile, Verification, and User Information Symbols'
RF2STEGT8–Network of user icons and encryption process image over computer code
RF3CG4JX5–Person logging into laptop with digital padlock icons and secure login button. Concept of cybersecurity, two-factor authentication, data protection, p
RF2TBJF1W–User ID Card Icon on Speech Glass Morphism Bubble Realistic Symbol on Dark Pink Studio Background. 3D Render Illustration.
 Authentication isometric concept. Password, login authorization fingerprint access. Data safe and protection landing vector page. Illustration of login verification approvement, authorize Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-isometric-concept-password-login-authorization-fingerprint-access-data-safe-and-protection-landing-vector-page-illustration-of-login-verification-approvement-authorize-image357388144.html
Authentication isometric concept. Password, login authorization fingerprint access. Data safe and protection landing vector page. Illustration of login verification approvement, authorize Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-isometric-concept-password-login-authorization-fingerprint-access-data-safe-and-protection-landing-vector-page-illustration-of-login-verification-approvement-authorize-image357388144.htmlRF2BNCC68–Authentication isometric concept. Password, login authorization fingerprint access. Data safe and protection landing vector page. Illustration of login verification approvement, authorize
RF2NM085F–Default Avatar Female Profile. User profile icon. Profile picture, portrait symbol. User member, People icon in flat style. Circle button with avatar.
 Sign in web page concept. Account login and password form page on screen. Sign in to account, user authorization, login authentication page concept. 3d Vector Illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/sign-in-web-page-concept-account-login-and-password-form-page-on-screen-sign-in-to-account-user-authorization-login-authentication-page-concept-3d-vector-illustration-image643437746.html
Sign in web page concept. Account login and password form page on screen. Sign in to account, user authorization, login authentication page concept. 3d Vector Illustration Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/sign-in-web-page-concept-account-login-and-password-form-page-on-screen-sign-in-to-account-user-authorization-login-authentication-page-concept-3d-vector-illustration-image643437746.htmlRF2SAR3BE–Sign in web page concept. Account login and password form page on screen. Sign in to account, user authorization, login authentication page concept. 3d Vector Illustration
 Digital Identity and Security Authentication as a Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-identity-and-security-authentication-as-a-concept-image376779114.html
Digital Identity and Security Authentication as a Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-identity-and-security-authentication-as-a-concept-image376779114.htmlRF2CTYNGX–Digital Identity and Security Authentication as a Concept
 Two-step authentication and verification online internet account login concept. Casual adult caucasian freelancer man is using smartphone and laptop c Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-authentication-and-verification-online-internet-account-login-concept-casual-adult-caucasian-freelancer-man-is-using-smartphone-and-laptop-c-image327649448.html
Two-step authentication and verification online internet account login concept. Casual adult caucasian freelancer man is using smartphone and laptop c Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-authentication-and-verification-online-internet-account-login-concept-casual-adult-caucasian-freelancer-man-is-using-smartphone-and-laptop-c-image327649448.htmlRF2A11M60–Two-step authentication and verification online internet account login concept. Casual adult caucasian freelancer man is using smartphone and laptop c
 Internet user authentication system with username and password, cyber security concept Network security and privacy technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-user-authentication-system-with-username-and-password-cyber-security-concept-network-security-and-privacy-technology-image544668765.html
Internet user authentication system with username and password, cyber security concept Network security and privacy technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-user-authentication-system-with-username-and-password-cyber-security-concept-network-security-and-privacy-technology-image544668765.htmlRF2PJ3PFW–Internet user authentication system with username and password, cyber security concept Network security and privacy technology
 PC with login and password form page on screen, registration page. Sign in page, user authorization. Login authentication concept on laptop screen. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/pc-with-login-and-password-form-page-on-screen-registration-page-sign-in-page-user-authorization-login-authentication-concept-on-laptop-screen-image452074239.html
PC with login and password form page on screen, registration page. Sign in page, user authorization. Login authentication concept on laptop screen. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/pc-with-login-and-password-form-page-on-screen-registration-page-sign-in-page-user-authorization-login-authentication-concept-on-laptop-screen-image452074239.htmlRF2H7DN8F–PC with login and password form page on screen, registration page. Sign in page, user authorization. Login authentication concept on laptop screen.
RF3AJ04DK–User and Account Icons Collection.
 Abstract corporate company office employee id card or identity card design layout with blue and green color. Modern creative identification card Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/abstract-corporate-company-office-employee-id-card-or-identity-card-design-layout-with-blue-and-green-color-modern-creative-identification-card-image696850425.html
Abstract corporate company office employee id card or identity card design layout with blue and green color. Modern creative identification card Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/abstract-corporate-company-office-employee-id-card-or-identity-card-design-layout-with-blue-and-green-color-modern-creative-identification-card-image696850425.htmlRF3CDM7R5–Abstract corporate company office employee id card or identity card design layout with blue and green color. Modern creative identification card
 Internet security shield concept. Cyber security data protection business technology. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-security-shield-concept-cyber-security-data-protection-business-technology-image551620752.html
Internet security shield concept. Cyber security data protection business technology. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-security-shield-concept-cyber-security-data-protection-business-technology-image551620752.htmlRF2R1CDW4–Internet security shield concept. Cyber security data protection business technology.
 Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image239116963.html
Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image239116963.htmlRFRW0M3F–Remote Authentication in Dial In User Service. Telecommunications Networks Concept.
 Conceptual display Authorized User. Word for person granted permission to manage access or make decisions Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-authorized-user-word-for-person-granted-permission-to-manage-access-or-make-decisions-image550381820.html
Conceptual display Authorized User. Word for person granted permission to manage access or make decisions Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-authorized-user-word-for-person-granted-permission-to-manage-access-or-make-decisions-image550381820.htmlRF2PYC1HG–Conceptual display Authorized User. Word for person granted permission to manage access or make decisions
RFP5YHFD–Login user interface with user icon
RF3BACJE7–Vector profile icons for user identification and avatars
 two factor authentication online card mobile phone Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-factor-authentication-online-card-mobile-phone-image475934693.html
two factor authentication online card mobile phone Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-factor-authentication-online-card-mobile-phone-image475934693.htmlRF2JJ8KFH–two factor authentication online card mobile phone
RF3BNHRJ6–'ID Card Icons - Profile, Verification, and User Information Symbols'
RF2YPDYT0–Image of, European Union stars over network of connected user icons and binary code
 User Login Interface. Username And Password Login Vector Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-login-interface-username-and-password-login-vector-image546182855.html
User Login Interface. Username And Password Login Vector Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/user-login-interface-username-and-password-login-vector-image546182855.htmlRF2PMGNPF–User Login Interface. Username And Password Login Vector
 Data secure. Banner with user login laptop. Data protection. Vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-secure-banner-with-user-login-laptop-data-protection-vector-illustration-image472673699.html
Data secure. Banner with user login laptop. Data protection. Vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/data-secure-banner-with-user-login-laptop-data-protection-vector-illustration-image472673699.htmlRF2JD043F–Data secure. Banner with user login laptop. Data protection. Vector illustration.
 Showing badge. Security access identification pass card. Businessman and businesswoman in business suit show id badges. Vector concept identification employee, photo user woman and man Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/showing-badge-security-access-identification-pass-card-businessman-and-businesswoman-in-business-suit-show-id-badges-vector-concept-identification-employee-photo-user-woman-and-man-image357376340.html
Showing badge. Security access identification pass card. Businessman and businesswoman in business suit show id badges. Vector concept identification employee, photo user woman and man Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/showing-badge-security-access-identification-pass-card-businessman-and-businesswoman-in-business-suit-show-id-badges-vector-concept-identification-employee-photo-user-woman-and-man-image357376340.htmlRF2BNBW4M–Showing badge. Security access identification pass card. Businessman and businesswoman in business suit show id badges. Vector concept identification employee, photo user woman and man
RF2SJETGH–Silhouette head, avatar face, male person icon. User member, People icon in flat style. Circle button with avatar photo silhouette vector design and i
RF2JP419Y–authentication line icon, outline symbol, vector illustration, concept sign
 Digital Identity and Security Authentication as a Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-identity-and-security-authentication-as-a-concept-image273720791.html
Digital Identity and Security Authentication as a Concept Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/digital-identity-and-security-authentication-as-a-concept-image273720791.htmlRFWW91JF–Digital Identity and Security Authentication as a Concept
 Two-step authentication and verification online internet account login concept. Casual adult caucasian freelancer man is using smartphone and laptop c Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-authentication-and-verification-online-internet-account-login-concept-casual-adult-caucasian-freelancer-man-is-using-smartphone-and-laptop-c-image262840701.html
Two-step authentication and verification online internet account login concept. Casual adult caucasian freelancer man is using smartphone and laptop c Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-authentication-and-verification-online-internet-account-login-concept-casual-adult-caucasian-freelancer-man-is-using-smartphone-and-laptop-c-image262840701.htmlRFW7HBYW–Two-step authentication and verification online internet account login concept. Casual adult caucasian freelancer man is using smartphone and laptop c
 Internet user authentication system with username and password, cyber security concept Network security and privacy technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-user-authentication-system-with-username-and-password-cyber-security-concept-network-security-and-privacy-technology-image544667773.html
Internet user authentication system with username and password, cyber security concept Network security and privacy technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/internet-user-authentication-system-with-username-and-password-cyber-security-concept-network-security-and-privacy-technology-image544667773.htmlRF2PJ3N8D–Internet user authentication system with username and password, cyber security concept Network security and privacy technology
RF3BMTPW0–Fingerprint Icon for Biometric Identity, Secure Authentication, and Touch ID Scanner Access
RF3BGXJ0R–User Account Line Icons Set - Profile, Security, Login & Privacy Symbols
 Modern corporate creative and minimal employee id card or identity card design layout. Template design for business company identity card, id card Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/modern-corporate-creative-and-minimal-employee-id-card-or-identity-card-design-layout-template-design-for-business-company-identity-card-id-card-image683474498.html
Modern corporate creative and minimal employee id card or identity card design layout. Template design for business company identity card, id card Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/modern-corporate-creative-and-minimal-employee-id-card-or-identity-card-design-layout-template-design-for-business-company-identity-card-id-card-image683474498.htmlRF3BKXXKE–Modern corporate creative and minimal employee id card or identity card design layout. Template design for business company identity card, id card
 Woman showing interface login and password on tablet. Data protection and secured internet access. Concept of security network. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-showing-interface-login-and-password-on-tablet-data-protection-and-secured-internet-access-concept-of-security-network-image490841471.html
Woman showing interface login and password on tablet. Data protection and secured internet access. Concept of security network. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/woman-showing-interface-login-and-password-on-tablet-data-protection-and-secured-internet-access-concept-of-security-network-image490841471.htmlRF2KEFN8F–Woman showing interface login and password on tablet. Data protection and secured internet access. Concept of security network.
 Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image238273802.html
Remote Authentication in Dial In User Service. Telecommunications Networks Concept. Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/remote-authentication-in-dial-in-user-service-telecommunications-networks-concept-image238273802.htmlRFRRJ8JJ–Remote Authentication in Dial In User Service. Telecommunications Networks Concept.
 Conceptual display Authorized User. Word for person granted permission to manage access or make decisions Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-authorized-user-word-for-person-granted-permission-to-manage-access-or-make-decisions-image550385564.html
Conceptual display Authorized User. Word for person granted permission to manage access or make decisions Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/conceptual-display-authorized-user-word-for-person-granted-permission-to-manage-access-or-make-decisions-image550385564.htmlRF2PYC6B8–Conceptual display Authorized User. Word for person granted permission to manage access or make decisions
 Cloud computing, web service, user holding data folder, uploading files to cloud storage Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cloud-computing-web-service-user-holding-data-folder-uploading-files-to-cloud-storage-image417498104.html
Cloud computing, web service, user holding data folder, uploading files to cloud storage Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/cloud-computing-web-service-user-holding-data-folder-uploading-files-to-cloud-storage-image417498104.htmlRF2F76K2G–Cloud computing, web service, user holding data folder, uploading files to cloud storage
 Authentication by facial recognition or face detection. Biometric security system. Cybersecurity tech concept. Business and technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-by-facial-recognition-or-face-detection-biometric-security-system-cybersecurity-tech-concept-business-and-technology-image547224184.html
Authentication by facial recognition or face detection. Biometric security system. Cybersecurity tech concept. Business and technology Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/authentication-by-facial-recognition-or-face-detection-biometric-security-system-cybersecurity-tech-concept-business-and-technology-image547224184.htmlRF2PP860T–Authentication by facial recognition or face detection. Biometric security system. Cybersecurity tech concept. Business and technology
 two factor authentication online card mobile phone Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-factor-authentication-online-card-mobile-phone-image475934308.html
two factor authentication online card mobile phone Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-factor-authentication-online-card-mobile-phone-image475934308.htmlRF2JJ8K1T–two factor authentication online card mobile phone
RF3CHTHCN–Cybersecurity and Biometric Identity Authentication System. Person using fingerprint scanning technology with icons represent security protocols, data
 Two-step verification flat illustration vector template, OTP, Authentication password, One-time password for secure transaction Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-verification-flat-illustration-vector-template-otp-authentication-password-one-time-password-for-secure-transaction-image633930095.html
Two-step verification flat illustration vector template, OTP, Authentication password, One-time password for secure transaction Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/two-step-verification-flat-illustration-vector-template-otp-authentication-password-one-time-password-for-secure-transaction-image633930095.htmlRF2YRA08F–Two-step verification flat illustration vector template, OTP, Authentication password, One-time password for secure transaction
RF2RC2KP6–Banner of zero trust vector illustration security model with the icon of security, WIFI, cloud service, mutual authentication, check, network
 Login user interface. Modern screen design for mobile app and web design. Gradient background. Website element. Vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/login-user-interface-modern-screen-design-for-mobile-app-and-web-design-gradient-background-website-element-vector-illustration-image245018018.html
Login user interface. Modern screen design for mobile app and web design. Gradient background. Website element. Vector illustration. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/login-user-interface-modern-screen-design-for-mobile-app-and-web-design-gradient-background-website-element-vector-illustration-image245018018.htmlRFT6HEYE–Login user interface. Modern screen design for mobile app and web design. Gradient background. Website element. Vector illustration.
 Unrecognizable clinician accessing secure document on approved specialty drug. Pharma IT concept for access control, user authorization, compliance, l Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/unrecognizable-clinician-accessing-secure-document-on-approved-specialty-drug-pharma-it-concept-for-access-control-user-authorization-compliance-l-image594994582.html
Unrecognizable clinician accessing secure document on approved specialty drug. Pharma IT concept for access control, user authorization, compliance, l Stock Photohttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/unrecognizable-clinician-accessing-secure-document-on-approved-specialty-drug-pharma-it-concept-for-access-control-user-authorization-compliance-l-image594994582.htmlRF2WG09JE–Unrecognizable clinician accessing secure document on approved specialty drug. Pharma IT concept for access control, user authorization, compliance, l
RF2T2T44Y–Signing up and logging in Private account, SECURE ACCESS. User. Profile Security Lock. Account password. Login. icon set.
 Online Registration Form on laptop screen, Register Button. Registration or sign up user interface. Users use secure login and password. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-registration-form-on-laptop-screen-register-button-registration-or-sign-up-user-interface-users-use-secure-login-and-password-image474945457.html
Online Registration Form on laptop screen, Register Button. Registration or sign up user interface. Users use secure login and password. Stock Vectorhttps://www.alamy.com/image-license-details/?v=1https://www.alamy.com/online-registration-form-on-laptop-screen-register-button-registration-or-sign-up-user-interface-users-use-secure-login-and-password-image474945457.htmlRF2JGKHNN–Online Registration Form on laptop screen, Register Button. Registration or sign up user interface. Users use secure login and password.